
The Importance of Context-Aware IAM and Continuous Risk and Trust Analysis – Notes from Gartner IAM summit

By Dana Tamir, VP Market Strategy, Silverfort
Earlier this month I attended the Gartner Identity and Access Management Summit 2018 in Las Vegas. The summit was a great opportunity to meet with our customers and partners, as well as spend time with Gartner analysts. There were many interesting sessions delivered by analysts, vendors and end-users, sharing experiences, discussing best practices and recommended strategies – I wish I had time to attend more of the sessions. Nevertheless, I was able to attend some of them. Here are my notes:
Concerns about identity-based attacks are driving both identity and security teams to search for solutions that can better adapt to today’s evolving threat landscape. According to Gartner’s Mary Ruddy and Gregg Kreizman, improving security and access controls is not just about technologies, but a need to adopt a new mindset and new processes which will be amplified by technologies to deliver results. They introduced the ContinuousNEXT approach which is a strategy to achieve success in a world that is constantly changing.
CARTA, Gartner’s recommended Continuous Adaptive Risk and Trust Assessment (CARTA) approach is a key strategy that was discussed in sessions by Gartner’s Ant Allan, Khushbu Pratap (and probably others). According to Gartner, traditional events-based approaches to security are not effective enough against advanced, targeted attacks. Gartner recommends a more cohesive approach based on Continuous Adaptive Risk and Trust Assessments.
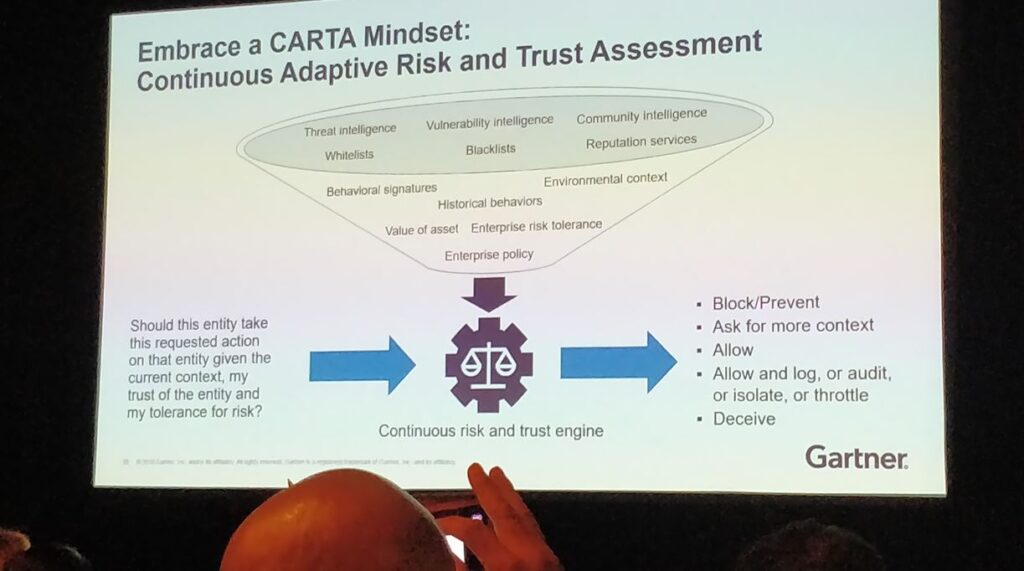
If in the past we used a monolithic approach towards IAM, today we need to think about ways to extend IAM, adapt to changing requirements and support better decision making. To do that we need to analyze more data. The better our identity contextual data is, the better our analytics will be, and the better support we will be able to provide for decision making. Access is not a one-time decision, they explained. You need to continuously assess everything and adapt accordingly.
In order to make IAM more extensible, we need to enable better data gathering and analysis. Identity is becoming smarter. As IAM becomes smarter, we should borrow “brains” from security systems like UEBA and banking fraud systems. The need to extend IAM technologies, the need to receive external feeds and respond to it was a recurring theme in many sessions.
We typically focus on blocking and preventing threats with a one-time approach. Complete protection requires us to block and prevent as well as detect and respond. We need to be more proactive, continually assess and follow up on the decision that was made. Continuous visibility and assessment need to consider the users, systems, activity, payload and network.
CARTA applies to identity and access management as well as threat protection. Access should be adaptive – look for the context of each transaction. Today, in most organizations, context assessment isn’t taking place, yet it is super important. It helps you understand what behavior sequence took place.
Don’t forget discovery requirements – you need to adapt to changes in your environment: new users, new devices, new systems. You need to predict how they will be used and plan accordingly. Therefore, you should continuously prioritize risk and re-assess the scope.
I also attended some vendor sessions:
Google explained the BeyondCorp security model they use to improve security yet simplify access. Google says you shouldn’t trust your corporate network. Instead, you should think about context-aware access. Google enriches each user’s authentication request with context – who is the user? How long ago since the user last authenticated? How did the user authenticate? From which device and location? All that information is processed in a central rules engine to determine if access should be granted and enforce the policy.
Microsoft talked about digital transformation and the move to the cloud. Azure Active Directory handles more than 200 million sessions at any time. And more than 25 million unique users used Entra ID (formerly Azure AD) to authenticate to 3rd party services. Microsoft sees identity as the new control plain. They also look for contextual data about each authentication request to evaluate the session risk and the effective policy, before granting access to resources – in the cloud or on premises. In addition, they highly recommend enforcing MFA to strengthen authentication and ensure authorized access.
As mentioned, there were many other interesting sessions I wish I had time to attend. Perhaps next year…
Table Of Contents
My Final Notes
It was interesting to learn how much Silverfort is aligned with Gartner’s recommendations – specifically the CARTA approach and the need to continuously assess risk and trust and adapt to changes in the organizations, as well as emerging threats.
Silverfort analyzes all access requests across on-premises and cloud environments, adding contextual data and leveraging an AI-based risk engine to assess the risk associated with each transaction. It then applies the appropriate security policy – allowing access, denying it, or requiring the user to perform additional authentication and validate his/her identity before making the decision.
Unlike all other solutions, Silverfort can monitor and protect every access without relying on agents or proxies, and can, therefore protect access to any asset, including proprietary systems, homegrown applications and IoT devices. Since Silverfort analyzes all access activity to on-premises and cloud resources, it analyzes hundreds of access requests per user per day, gaining unparalleled visibility and context about user’s behaviors. This enables Silverfort to continuously assess risk and effectively adapt access policies as needed, such as with our adaptive risk based authentication solution
Dana Tamir, VP Market Strategy, Silverfort
Dana is a veteran of the cybersecurity industry with over 15 years of real-world expertise and leadership roles in leading security companies. Prior to Silverfort, Dana served as VP Marketing at Indegy. Before that, she served as Director of Enterprise Security at Trusteer (acquired by IBM in 2012). She also held various roles at Imperva, Symantec, Bindview, and Amdocs. Dana holds an engineering degree from the Technion – Israel Institute of Technology, in addition to a number of industry and vendor certifications.
To learn more about Silverfort and see a demo, contact us today!
To learn more about Silverfort and how it can provide context-aware adaptive identity and access management as well as threat protection, please contact us.